January 29, 2026
·
2 min read
If you’re located outside the United States and trying to subscribe to Gemini Pro, you might have encountered the frustrating “Not available in your region” message. This guide explains why this happens and how to fix it.
Read the full text -> A total of 0.51k words
January 13, 2026
·
4 min read

Vim is a powerful command-line text editor that’s been around for decades, and it’s still widely used today. Whether you’re SSH-ing into a remote server or just prefer the keyboard-centric workflow, Vim is often the go-to choice. The learning curve can be steep at first — I remember the first time I opened Vim and couldn’t even figure out how to quit. But once you get the hang of it, the efficiency gains are real. This cheatsheet covers the essentials I use most often, and I’m trying to condense them.
Read the full text -> A total of 0.81k words
October 16, 2025
·
8 min read
This article is my understanding of the ERC-8004: Trustless Agents, which is a standard for Identity Registry, Reputation Registry and Verification Registry. And refer to the Ethereum Improvement Proposals ERC-8004: Trustless Agents.
Read the full text -> A total of 1.67k words
October 13, 2025
·
1 min read
I ran into a stubborn GitHub notification blue dot that wouldn’t go away even though the Notifications page showed nothing. Here’s the quick, safe way I found to resolve it, plus a few alternatives and notes on why it happens.
Read the full text -> A total of 0.34k words
October 12, 2025
·
1 min read
System Integrity Protection (SIP) is a security layer that limits even the root user from modifying protected parts of the system. Apple introduced it in OS X El Capitan to reduce the blast radius of malware and accidental system damage. In practice, SIP blocks writes to system locations, prevents runtime injection into protected processes, and restricts some kernel/system-level operations.
Sometimes I run a command and see ‘Operation not permitted’ despite sudo, SIP is often the reason. So I need to disable SIP temporarily.
Read the full text -> A total of 0.38k words
August 21, 2025
·
0 min read
Sometimes you encounter a large repository but only need a few directories from it. Cloning the entire repo wastes both time and disk space. Git’s sparse checkout solves this problem by letting you pull only the parts you need.
Read the full text -> A total of 0.12k words
June 22, 2025
·
0 min read

The Automator is a powerful tool for automating tasks on macOS. It allows you to create custom workflows that can be triggered by various events, such as opening a file, pasting text, or receiving an email. This article will share my common usages of Automator.
Read the full text -> A total of 0.11k words
June 19, 2025
·
3 min read
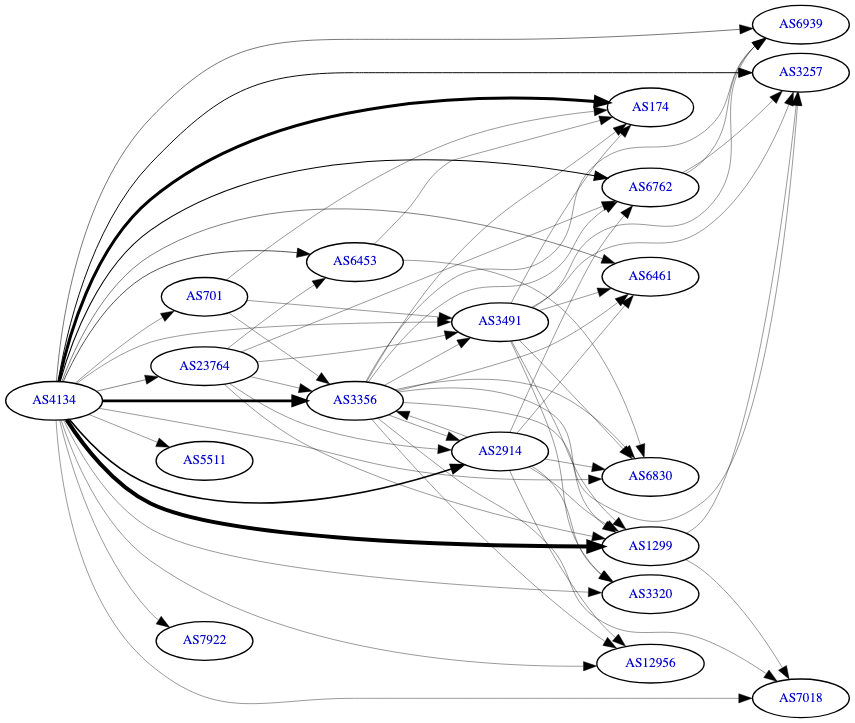
The performance and reliability of internet connectivity to and from mainland China are determined by a complex web of different network circuits, each with its own characteristics.
We will explore the crucial differences between the standard public network backbones, like the workhorse 163 network, and premium, optimized lines like CN2. We’ll also explain what dedicated networks such as IPLC are and why they offer a completely different level of performance and privacy. By the end of this article, you’ll have a clear framework for understanding these circuits, helping you make more informed decisions whether you’re choosing a hosting provider, diagnosing network issues, or are simply curious about how the internet infrastructure in mainland China operates.
Read the full text -> A total of 0.79k words
June 6, 2025
·
7 min read
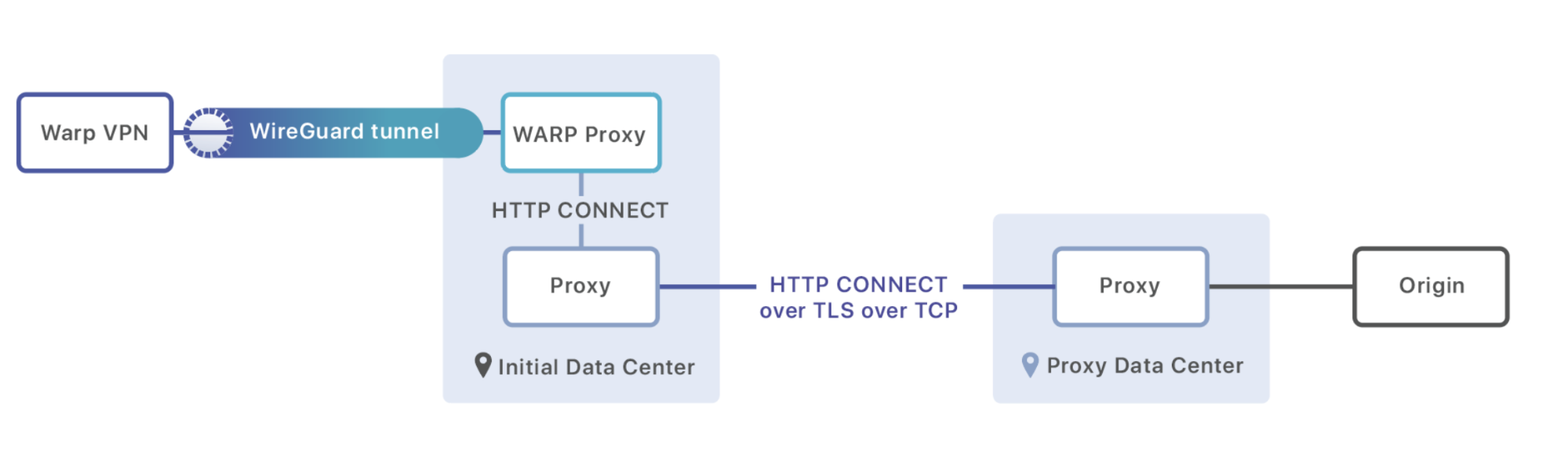
Frankly speaking, the first time I heard about Cloudflare is the service so called Cloudflare WARP which is provided by Cloudflare. Nowadays, you must have heard the fastest and private network can be provided by Cloudflare. If I say Cloudflare achieves the fastest object by the first step to visiting any website, the world’s fastest public DNS 1.1.1.1. You can probably guess the private provider, yes, that is Cloudflare WARP. So this article I will introduce the Cloudflare WARP further zero trust and how to use it.
Read the full text -> A total of 1.46k words
June 4, 2025
·
5 min read
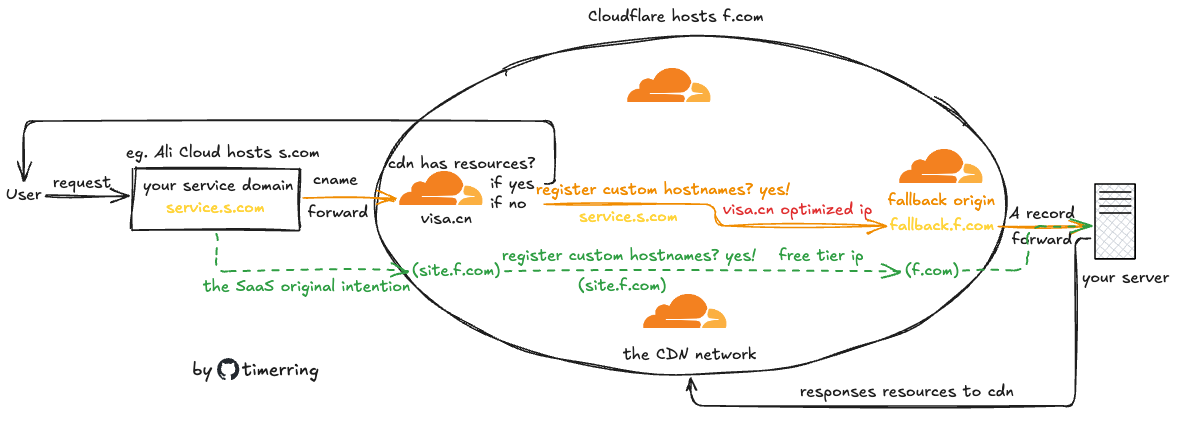
In common situation, when you use the cloudflare to resolve your domain name, and you choose to use the cloudflare proxy(the yellow cloud icon), then cloudflare would probably get your domain resources into their CDN, that could be a good thing, but as we know, the network in mainland has some special rules, so for the free tier user, the access to the resources in the CDN would be somehow worse, even rest. That means, if the user connect to the node which has high latency, the request will experience worse. So this article will introduce some methods to help your resources access to the cloudflare nodes which are optimized for the mainland.
Read the full text -> A total of 1.06k words






